In this post, NeuraLegion’s VP Oliver Moradov explains how you can use Cypress, NeuraLegion’s HAR Generator, and NexPloit together to automate AppSec testing in your pipelines. NeuraLegion delivers a developer and QA focused AI-powered Dynamic Application Security Testing (DAST) SaaS platform. With no-false positives and able to scan multiple protocols across web, mobile & API, QA can scan for security issues using their existing functional scripts and Cypress tests, at speed.
As a company whose raison d'être is enabling companies to automate security testing as part of their pipeline, enabling our teams with the right tools to underpin our own internal culture of automation, whether functional or security testing, has been important from the start.
NeuraLegion’s Adoption of Cypress
Like our clients, we continually enhance our product and add new features and capabilities to continue to stay ahead. We have rapid release cycles, and all our teams are focused on delivering software at a breakneck scale and speed.
As our team began to expand, we started to run even more concurrent builds, just like our clients who are continually embracing DevOps and CI/CD. QA automation (QAA) with tools like Cypress make functional testing a seamless part of this process to make sure the application works as intended.
Developers, including ours, are often asked to wear multiple hats, and security testing is one of them—we have a pretty amazing security team, but everyone is part of the solution. Successful quality control begins at the unit test level, where bugs are the easiest to detect (and certainly the cheapest to fix).
Making Cypress work with our NexPloit Engine
We quickly enlisted our QA colleagues to help in the security testing process as well. They make great security testers because they spend much of their time thinking not just about how something can and should be used, but all the ways it can and will be misused as well. It enabled us to add another layer of security testing as an additional check, without adding much more work to their already busy schedule.
We wanted to leverage our existing functional scripts and tests to perform security tests against our application and API, while keeping up with the rapid pace we set for ourselves. Our Nexploit.app platform can consume HAR files to run security tests, and we wanted to generate these files from our Cypress tests so our QA could run these for us...enter the NeuraLegion Cypress HAR Generator!
Integrating and Configuring Cypress Har Generator and NexPloit
Here you’ll see how you too can start to generate these HAR files from your Cypress tests and to run comprehensive security tests against your targets.
For this example, we will
- Use a vulnerable application to run some functional tests against its login page
- Go through the installation of and automatically save the tests as a HAR file (HTTP Archive File), using NeuraLegion’s Cypress HAR Generator
- Use this to run a security test using the HAR file with NeuraLegion’s NexPloit.app
You can follow along too...you’ll need:
- To set up a free NexPloit.app account to run the security tests.
- The code repository for this example, which contains a publicly available repository of an example vulnerable application. Feel free to use this target as a test project.
First up, you’ll need to install the Cypress HAR Generator
We suggest you install the NPM as a development dependency—this can be found here:
npm i --save-dev @neuralegion/cypress-har-generator
Once that's completed, you can then set up a plugin to configure commands which it provides.
In the Cypress directory, enter the following code in your cypress/plugin/index.js file:
install(on as any;
on('before:browser:launch', (browser, launchOptions) => {
ensureBrowserFlags(browser, launchOptions);
return launchOptions;
});
};You then need to register commands that perform the manipulation with the HAR file.
Add this module to your support file cypress/support/index.js:
@neuralegion/cypress-har-generator/commands
Once completed, we need to describe a few built in cypress hooks to control the flow:
As seen in the above example:
- Start recording
- Will save HAR into the root folder by default - the destination of the folder can be changed by either
- Using environment variables, or
- Passing additional parameters, such as outDir as per the example below
For this example, we will use Environment Variables, and navigate to package.json to add these parameters:
If you prefer to go into headless mode, you can use this command:
Please note that you can change the proxy, to use Docker Compose, run a local host or against a publicly facing application. In our example, we will be using our vulnerable application Broken Crystals.
We can now start to run tests:
Once Cypress has finished executing the test, the plugin will save a new HAR in the folder previously specified
This file can now be used to run a security scan against the same target using the NexPloit.app.
As a developer-focused technology, NexPloit.app can be integrated with GitHub Actions, CircleCI, JFrog and AzureDevOps amongst others, to run scans against every commit, PR or merge to master with a specific HAR file branch that can leverage the HAR file generated with Cypress. In this example, we will demonstrate this via the NexPloit.app UI.
If you haven't already, you can sign up for a free account here and be up and scanning your applications and APIs for security vulnerabilities in minutes.
In your NexPloit.app dashboard go to New Scan
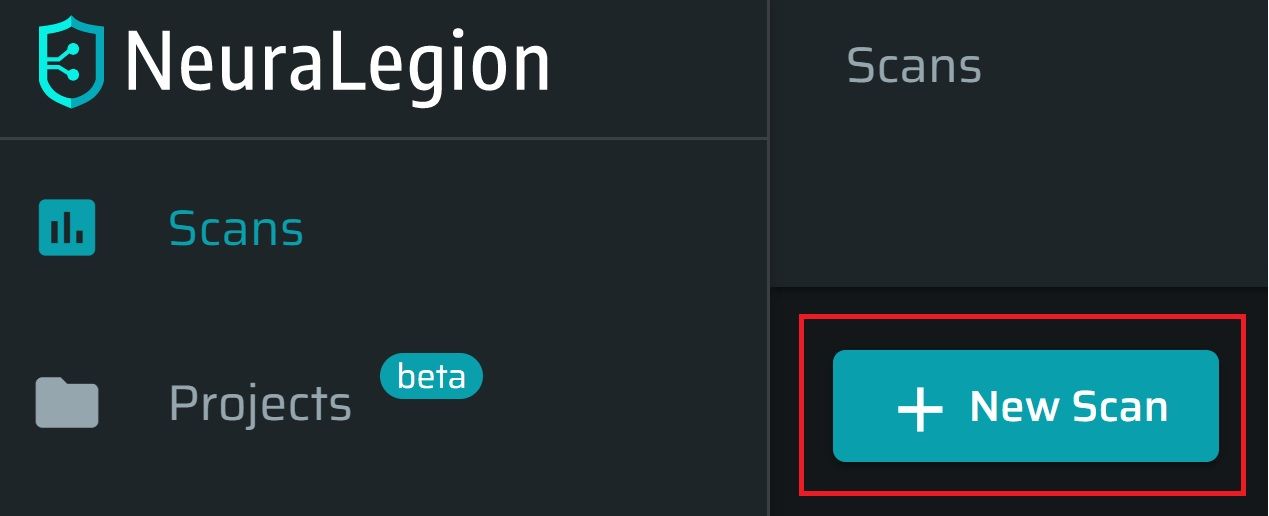
This will open up the manual scan configuration window, below.
You can then upload the HAR file generated to the NexPloit engine, which will be used to define the scope of the test against the target and enable NexPloit to build the attack surface and start the tests.
You will see that the hosts detected in the HAR file will be shown and will need to be selected accordingly to those you have control over and of course the permission to scan
You will also see NexPloit’s built-in Scan Optimisation settings.
These remove the need for developers and QA to be security experts and enables our engine to do the heavy lifting in terms of automatically running the right tests against the target, while reducing scan speeds without compromising on scan quality
- Smart Scan: Uses automatic smart decisions such as: parameter skipping, detection phases, etc. to minimize scan time. When turned off, all the tests will run on all the parameters, which increases the coverage at the expense of scan time.
- Skip Static parameters: Use an advanced algorithm to automatically determine if a parameter has any effect on the target system's behavior when changed, and skip testing such static parameters. Skipping static parameters greatly increases the scan speed, without compromising the scan coverage. Static parameters can include: style parameters like
javascript.version=, analytics related data and other kinds of metadata.
Please note that for those new to security testing in particular and/or for added speed and simplicity, you can also avail our Quick Start, Standard scan set up, where you can simply upload the file, name the scan and start scanning.
The scan you started will then be visible in your "My Scans" list.
Clicking on the scan name, you will be able to drill into the scan results and analysis; vulnerabilities are reported in real time as they are detected, so no need to wait for the scan to stop.
All vulnerabilities are automatically validated as security issues on the target, ready to be fixed, without the need for any manual validation (in line with our NO false positive reporting).
The results provide the QA and developer with everything they need to understand the issue, how to replicate, and more importantly, how to fix (with remediation guidelines):
The Request, with a diff-like view (what was added/deleted) is provided, as well as the Response, Headers and the Body.
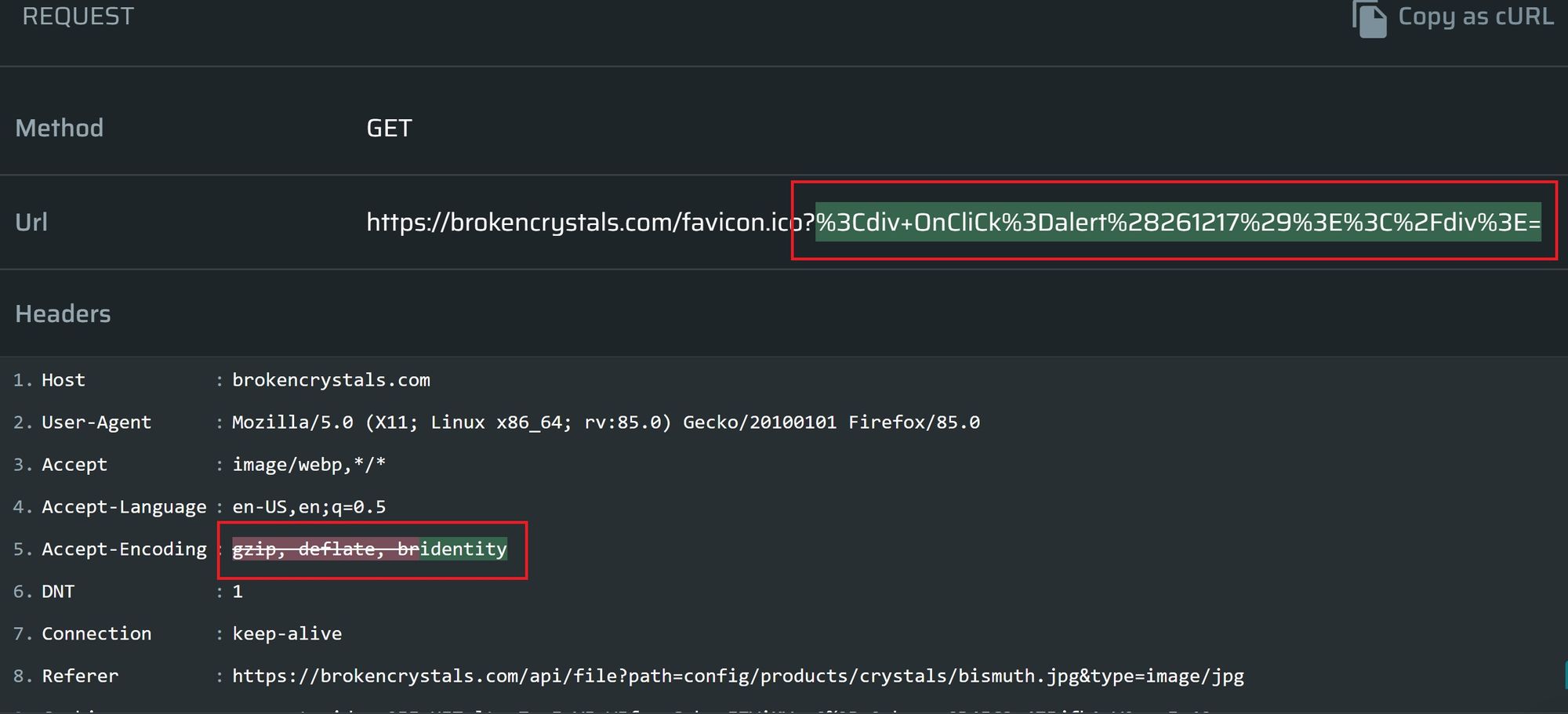
In this particular example, of an Cross-site Scripting (XSS) issue, we also provide additional evidence in the form of a screen shot as a proof of concept, so you know the vulnerability is there:
Nexploit integrates with JIRA so a ticket can be automatically raised with each issue detected. The request and response can also be copied as a cURL for debugging, to make things even easier.
Security Testing and QA, NeuraLegion and Cypress...great together!
We found that writing our tests in Cypress was easy and efficient, and in line with our security testing technology where we simplify the process to enable developers and QA to run security tests.
Connecting NeuraLegion’s DAST AppSec scanning into your pipeline is also really simple too, so you can continue to use your other CI integrations.
Whether testing your web apps or APIs (SOAP, REST, GraphQL), the results produced are organized in a developer friendly way and as a QA, can help establish a culture of security testing and let you champion security testing.
Go ahead and try it out for free!
